 This has been proven true by incidents broadcast around the world in minutes or hours after they have happened. Many have suffered the consequences of such incidents in the UK, US and mostly each and every place on earth where people have had their information taken and used for no good before there was even a sign that there was a problem.
This has been proven true by incidents broadcast around the world in minutes or hours after they have happened. Many have suffered the consequences of such incidents in the UK, US and mostly each and every place on earth where people have had their information taken and used for no good before there was even a sign that there was a problem.
Big business has been reminded again and again that complacency is it’s worst enemy and they have failed again and again at the area. Why? Well first, total protection is almost always imperfect and somebody out there with enough intent and resources can break-in however expensive the protection methods may be. Next is that the best systems for protection is always the ones that cost too much yet they still remain vulnerable and hackable. Contrary to most ad’s you see in print, the internet or your Television there is no one true solution to protection, for if the hardware and software measures succeed in protecting you, the human behind the computer/s are always the biggest risk. That is why even the most expensive solutions are used in conjunction with other solutions to provide the best of both worlds combining physical and software solutions hoping that combination will be enough protection from the continuous influx of attacks from the web and elsewhere. Encryption is nice but it takes a lot of computing power to implement making it too expensive for implementation on all levels of the company. All of these high-tech solutions and hardware would be nothing if the people using the various computer systems in the said organization fail to use them so the weakest link in every system is still the human. Strict adherence and compliance is the key with systems that process information somewhat autonomously already in use doing the searching and classification of information without the user’s input. This uses the latest in Artificial Intelligence with minimal intervention or input from the users.


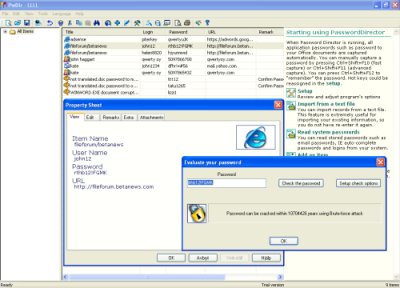 Are you like me who has the bad habit of forgetting the passwords to your online accounts? Except for sites I frequently visit, like those for web-based services, I can’t keep track and lose passwords all the time. There’s no true solution to this problem. I’ve tried using the same passwords for multiple accounts, but that’s pretty dangerous – if one of your accounts gets hacked, they can guess what sites you frequent and gain access to your data. Writing it down can be downright dangerous – it’s even easier to lose paper and notebooks during your daily routine. It also boils down to an issue of trust with the people you live and work with.
Are you like me who has the bad habit of forgetting the passwords to your online accounts? Except for sites I frequently visit, like those for web-based services, I can’t keep track and lose passwords all the time. There’s no true solution to this problem. I’ve tried using the same passwords for multiple accounts, but that’s pretty dangerous – if one of your accounts gets hacked, they can guess what sites you frequent and gain access to your data. Writing it down can be downright dangerous – it’s even easier to lose paper and notebooks during your daily routine. It also boils down to an issue of trust with the people you live and work with. 