McAfee, part of Intel Security, is one of the most popular brands in the IT security niche. Founded in 1987, the company has since then grown to become a household name, with people paying a premium for its products.
Today, the company announced the newest line of 2015 consumer security suites, which have been beefed up to address new threats and to provide added security for potential digital threats. The McAfee line of 2015 consumer security suites includes McAfee AntiVirus Plus 2015, McAfee Internet Security 2015, and McAfee Total Protection 2015. [Read more…]

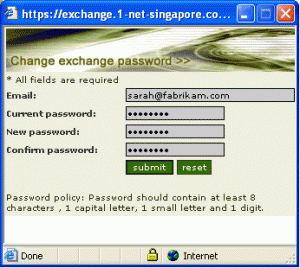
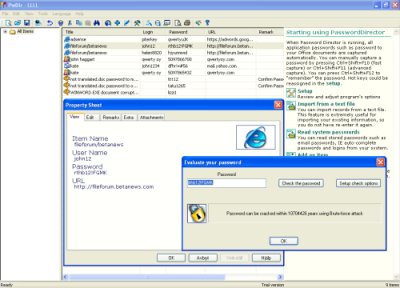 Are you like me who has the bad habit of forgetting the passwords to your online accounts? Except for sites I frequently visit, like those for web-based services, I can’t keep track and lose passwords all the time. There’s no true solution to this problem. I’ve tried using the same passwords for multiple accounts, but that’s pretty dangerous – if one of your accounts gets hacked, they can guess what sites you frequent and gain access to your data. Writing it down can be downright dangerous – it’s even easier to lose paper and notebooks during your daily routine. It also boils down to an issue of trust with the people you live and work with.
Are you like me who has the bad habit of forgetting the passwords to your online accounts? Except for sites I frequently visit, like those for web-based services, I can’t keep track and lose passwords all the time. There’s no true solution to this problem. I’ve tried using the same passwords for multiple accounts, but that’s pretty dangerous – if one of your accounts gets hacked, they can guess what sites you frequent and gain access to your data. Writing it down can be downright dangerous – it’s even easier to lose paper and notebooks during your daily routine. It also boils down to an issue of trust with the people you live and work with.