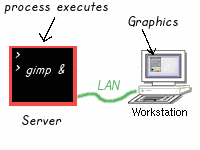
It is possible, using X11, the graphical system for UNIX and Linux, to display the interface to a program on another user’s X display. In order for this to happen, they have to allow access to their display, which is not the default, but it may be set on certain systems, especially poorly configured multi-user systems.
You can, of course, try this on any system. Simply run the command
xhost +
This removes access restrictions. Now, you can launch X programs as another user on the same machine, or as a user on a different machine, by setting your DISPLAY environment variable. For example, if an X session is running on 10.0.0.5 and access restrictions have been removed, it is possible to run Firefox on another computer, say, 10.0.0.26, and have it display on 10.0.0.5’s screen.
DISPLAY=”10.0.0.5:0″ firefox
Note that you don’t need to log in to 10.0.0.5 over SSH, the X system makes use of port 6000/tcp to communicate between the program and the X display.
The xhost – command can be used to enable access control, but on systems where it is useful to have other users share a display (for instance, if you have two user accounts but only one monitor, and want to use GUI applications from both accounts) the X port should be firewalled.
X11 uses TCP port 6000, and the following iptables command should prevent access to the X port from ethernet interfaces. Use wlan+ for wireless devices, or simply use -i ! lo to block all X access except from localhost.
iptables -A chainname -i eth+ -p tcp –dport 6000 -j DROP